Introduction
Biometric template protection comes down to threat models and transformation choices. Reversible transforms support re-issuance but risk exposure. Irreversible transforms improve privacy but can reduce matching performance. Template-on-card and match-on-device models mitigate theft by keeping raw templates off servers.
The Problem with Plain Biometric Templates
Raw biometric templates (fingerprint minutiae, iris codes, face embeddings) are not secrets in the same way as passwords. They:
Cannot be changed easily if leaked (you can reset a password, but not your fingerprint).
Are reusable across systems, creating a cross-matching risk if stored in plaintext.
Attract attackers who can exploit stolen templates for spoof creation or identity fraud.
Hence, template protection is a non-negotiable requirement in modern deployments.
What is Cancelable Biometrics?
Cancelable biometrics is an advanced security technique designed to protect the integrity and privacy of an individual's biometric data, such as a fingerprint or face scan. Instead of storing the raw biometric template, this method applies a specific and repeatable distortion or transformation to the data before it is stored.
The core principle is to create a new, "canceled" version of the biometric template that is unique to a specific application or device. If this transformed template is ever compromised in a data breach, it can be revoked and a new, different transformed template can be re-issued without compromising the user's actual, permanent biometric trait.
Approaches to Template Protection
Biometric template protection strategies fall into two broad categories:
Cryptographic Protections (Salt & Hash)
Hashing with Salt: Similar to password security, templates are hashed with a user-specific salt.
Good for 1:N identification in databases.
Ensures stolen hashes cannot be matched across systems.
Hashing alone loses tolerance to biometric variability (noise, partial capture).
Biometric Cryptosystems (e.g., Fuzzy Vault, Fuzzy Commitment):
Bind a cryptographic key to biometric data.
Matching works only if the biometric input is "close enough."
Enables key release only on successful authentication.
Computationally heavy; may increase false reject rates.
Cancelable Biometrics (Transformations)
Reversible Transforms: Apply distortion, random projection, or token-based transform before storage.
If compromised, revoke and re-issue new transform ("cancel" the template).
Preserves matching accuracy.
If transform secret leaks, attacker may recover original template.
Irreversible Transforms: Feature-space warping, biohashing, or non-invertible transforms.
Protects privacy even if transform leaks.
Strong against cross-database attacks.
Typically reduces matching accuracy compared to raw features.
Deployment Models: Where to Protect
Protection also depends on where the template lives and where matching happens:
Template-on-Card (ToC)
The template is stored on a smartcard or secure element.
User retains control.
Minimal server exposure.
Card loss = loss of authentication factor.
Match-on-Device (MoD)
Templates never leave the sensor device (e.g., smartphone).
Templates never transit networks.
Strong user privacy.
Limits use cases requiring central matching (e.g., large-scale ID).
Server-Side Matching
Templates centralized in a DB.
Efficient for large-scale identification (1:N).
Highest risk if DB is breached— requires strongest protection schemes (salting, cancelable transforms, or cryptographic binding).
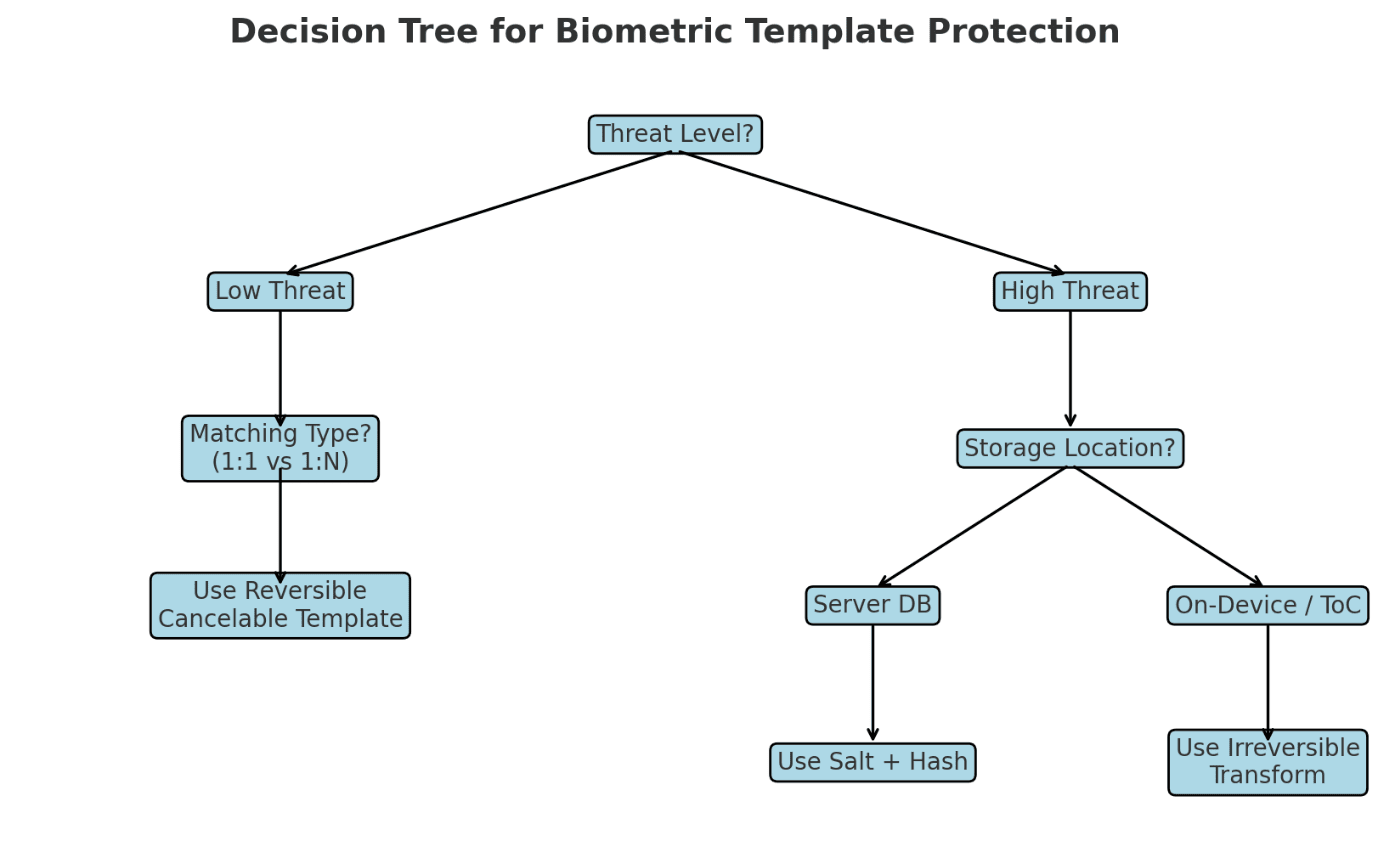
Decision Guide: When to Salt, Hash, or Transform
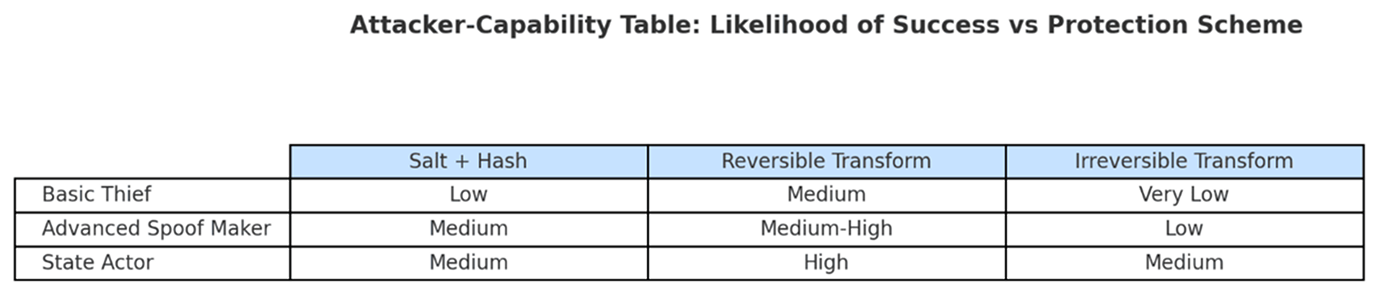
Think in terms of attacker capabilities and system needs:
Low-threat, convenience systems (workforce access):
Reversible cancelable templates often suffice.
High-value ID systems (national ID, border control):
Combine irreversible transforms + on-card/match-on-device.
Cloud or centralized servers:
Must use salted-hash + cancelable transform layering.
Fast-Start Checklist
Map threat model: insider theft, DB breach, spoofing.
Decide where to match: on-card, on-device, or server.
Choose protection layer:
Salt+hash for DBs.
Cancelable templates for re-issuance.
Irreversible transforms for privacy.
Validate with ISO/IEC 24745 (biometric template protection standard).
Test with real-world PAD (Presentation Attack Detection) scenarios.
Conclusion
No single scheme is universally best. A layered approach —cryptographic binding + cancelable transforms + secure storage—is the only way to ensure revocability, privacy, and spoof-resistance.
Ask for our template-security reference design to see how to integrate these protections into your biometric system.
Comments