Introduction
Access control is the foundation of modern security. Whether protecting physical spaces like offices and data centers or digital environments such as enterprise applications, the goal remains the same: to ensure only the right people, at the right time, can access sensitive information and resources. Access control systems are important in minimizing breaches, guaranteeing compliance, and ensuring business continuity by integrating identification, authentication, and authorization.
Access Control Systems Options
Four commonly known models of access control are given with their different strengths.
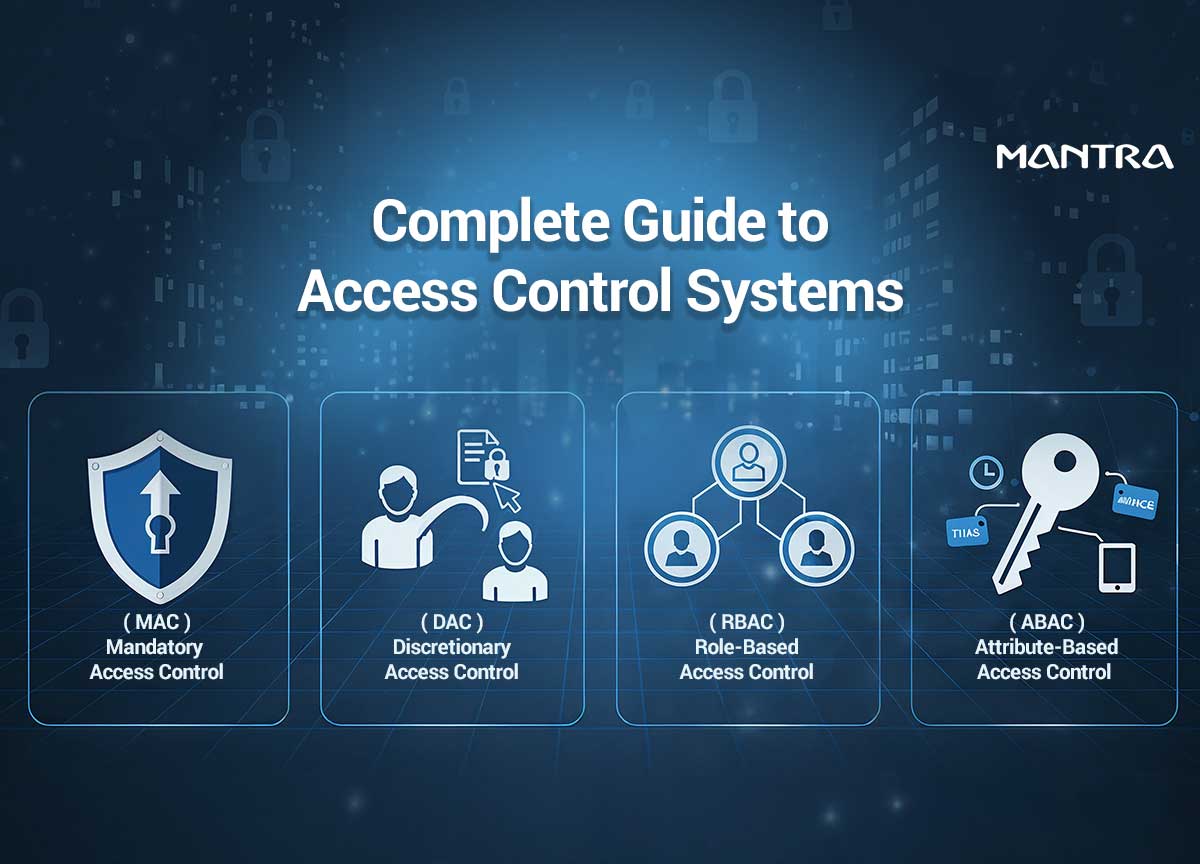
Mandatory Access Control (MAC) is the most restrictive model, where administrators alone decide permissions. It is highly secure and commonly used in government and defense because no user, not even resource owners, can change access rights.
Discretionary Access Control (DAC) shifts some authority to resource owners, allowing them to grant access to others. It makes DAC flexible and convenient, but also more prone to errors and oversight.
Role-Based Access Control (RBAC), the most common approach in enterprises, assigns permissions based on job roles. For example, HR staff can view employee records, while finance staff manage budgets. RBAC simplifies management and scales well across organizations.
Attribute-Based Access Control (ABAC) takes flexibility further by using attributes like location, device type, or time of access to decide permissions dynamically. It is context-aware and increasingly popular for cloud-based, distributed environments.
Core Components
All access control systems are constructed upon three fundamental components that interact to protect resources.

Identification -
Every user has been assigned an ID or digital profile that is distinct from other users within the system.

Authentication -
Verifies the user's identity through credentials such as passwords, biometrics, smart cards, or tokens.

Authorization -
Authorization is the procedure through which, after a successful authentication, the system determines what the user is allowed to access or what they are not allowed to access.
Combined, these three aspects constitute the foundation of access control, which guarantees security, accountability and traceability. To reinforce this even further, the audit logs document all attempts to access the system, and it is possible to trace actions and detect outliers.
Use Cases Across Industries
Access control systems are multi-purpose and are now a necessity in various industries:

Enterprise IT -
Limits unauthorized access to production systems and eliminates mistakes or violations.

Healthcare: -
This ensures that HIPAA is complied with by only allowing physicians to see patient records and the administration to see only billing data.

Financial Services -
Compliant with PCI DSS requirements by securing sensitive cardholder databases using RBAC and ABAC models.

Government and Defense -
MAC models are used to secure classified information, with permissions being defined solely by system administrators.

Manufacturing and Work Force Management -
Based on biometric attendance to eliminate proxy logins and enhance compliance monitoring.
The use cases underscore the adaptability of access control to industry-specific requirements without compromising security and regulatory compliance.
Implementation Best Practices
Implementation of an effective access control system demands that the organization embrace a series of good practices:
Principle of Least Privilege (PoLP): Do not give users more rights than they require to do their jobs.
Ban Shared Accounts: Use personal credentials to ensure accountability and traceability.
Periodic Access Audits: Check permissions regularly to detect dormant accounts or overprivileged accounts.
Multi-Factor Authentication (MFA): Enhance passwords with biometrics or tokens.
Zero Trust Security: Demand ongoing authentication rather than a single-use access authorization.
Employee Training: Train employees about access protocols to reduce human errors.
Automated Provisioning/Deprovisioning: Add efficiencies to the onboarding process and remove access promptly when employees are leaving.
By following these practices, organizations create a robust access control framework that balances usability with strong security.
Implementation Checklist
When planning an access control system, enterprises should:
Determine their security requirements and the resources they need to be protected.
Choose the right model: MAC-high security, RBAC-scale, ABAC-flexibility.
Implement authentication, ideally MFA with biometrics.
Build the system into currently available systems such as IAM, HRMS, and SIEM.
Automate onboarding and offboarding operations.
Be able to monitor and log anomalies.
Periodic audits to adhere to GDPR, HIPAA, PCI DSS, SOX, or DPDP.
Prepare AI-based improvements to dynamically change access.
The Future of Access Control and Compliance
The access control is not only a best practice but also a legal obligation, governed by regulatory frameworks, including GDPR, HIPAA, PCI DSS, SOX, and the DPDP Act in India. In the future, AI and machine learning can be used to develop the upcoming generation of systems that will allow real-time detection of anomalies, predictive risk control, and adaptive enforcement of policies. The transition will enable organizations to leave rigid permissions behind and proceed into more intelligent and self-adapting access ecosystems.
Conclusion
No longer is access control limited to keys and passwords, but biometrics, Zero Trust, and AI are developing advanced access control systems. Knowing the models that can be used and the best practices, organizations will be able to secure both physical and digital resources in addition to regulatory compliance. Done right, access control systems are a security and usability balance that cultivates trust and durability in a more digital first world.
FAQs
Financial services: To secure cardholder data per PCI DSS
Government and defense: To protect classified resources via MAC.
Manufacturing: To prevent proxy attendance and manage workforce access
Comments