
Introduction
Presentation Attack Detection (PAD) is a critical function within a biometric security system that determines whether a biometric sample being presented is from a live, authentic person or a fake artifact. In simpler terms, PAD is the technology that stops a system from being fooled by a "spoof," such as a photograph of a face, a video replay, or a silicone fingerprint.
What is a Presentation Attack?
A Presentation Attack is the act of presenting a fake biometric to a sensor. These fakes, also known as Presentation Attack Instruments (PAIs), can range from simple printed images to sophisticated, custom-made 3D masks or molds.
Presentation Attack Detection (PAD) testing has three levels - L1, L2, L3 (explained later) - each covering different spoofing complexities. Moreover, an iBeta PAD "pass" signals resistance to a certain tier of spoofs, but doesn't guarantee absolute spoof-proof security in the field.
The sole purpose of PAD is to analyze the incoming biometric sample and answer one fundamental question: "Is this a real, live person at the sensor right now?" It achieves this by looking for subtle signs of liveness and characteristics that are difficult to imitate, such as:
Micro-texture and reflection on skin.
Subtle movements like blinking or head motion.
Unique properties of human tissue (e.g., electrical conductivity or sub-surface patterns).
3D depth and shape.
The international standard ISO/IEC 30107 provides the framework for testing and measuring the effectiveness of PAD systems. By verifying that a system has strong PAD capabilities, organizations can ensure their biometric security is resilient against fraud and impersonation attempts.
Why ISO/IEC 30107 PAD Matters for Buyers
If you're procuring biometric devices, a "PAD certified" stamp can sound definitive. But what does it actually mean for your deployment- airport boarding, mobile banking, or workforce access?
The difference between PAD levels is critical. Misunderstanding what an "iBeta pass" means could lead to overpromises, deployment gaps, and costly missteps.
PAD Levels Simplified
ISO/IEC 30107-3 specifies PAD evaluations, but here's the plain-language buyer's breakdown:
Level 1 (L1):
Basic attacks-printed photos, replay videos, silicone fingers. Simulates consumer-grade threats.
Level 2 (L2):
More realistic spoofs-high-quality 3D masks, composite fingers, better materials. Harder to detect, but still lab-craft attacks.
Level 3 (L3):
Advanced adversary scenarios-custom molds, hyper-realistic masks, lab-grade fabrication. Represents attackers with serious resources.
Key Insight: Passing L1 does not equal L2 or L3 resistance. Each level is distinct and builds on the previous, but not automatically cumulative.
The iBeta "Pass"-What It Guarantees (and Doesn't)
Guarantees:
Device resisted specific attacks at that level, under lab test conditions.
Reports include APCER/BPCER, sometimes IAPAR/FMR/FNMR for full-system tests.
Doesn't Guarantee:
Coverage against future or unknown PAIs.
Spoof-proof security in uncontrolled, real-world environments.
Long-term resilience without ongoing re-testing or monitoring.
Myth vs Fact
| Myth | Fact |
|---|---|
| "iBeta L1 Certified means no one can spoof this device." | It only confirms the device blocked a limited set of L1 attacks under test-not that it's unbreakable. |
| "ISO certification = global seal of approval." | ISO defines the methods and metrics; labs report conformance. There's no "ISO badge." |
| "If I pass L2, I don't need L1." | Wrong. Vendors must clear L1 before attempting L2; the levels are cumulative in rigor. |
| "L3 is marketing fluff." | False. Launched June 2025, L3 introduces custom PAIs and stronger adversary models for high-risk deployments. |
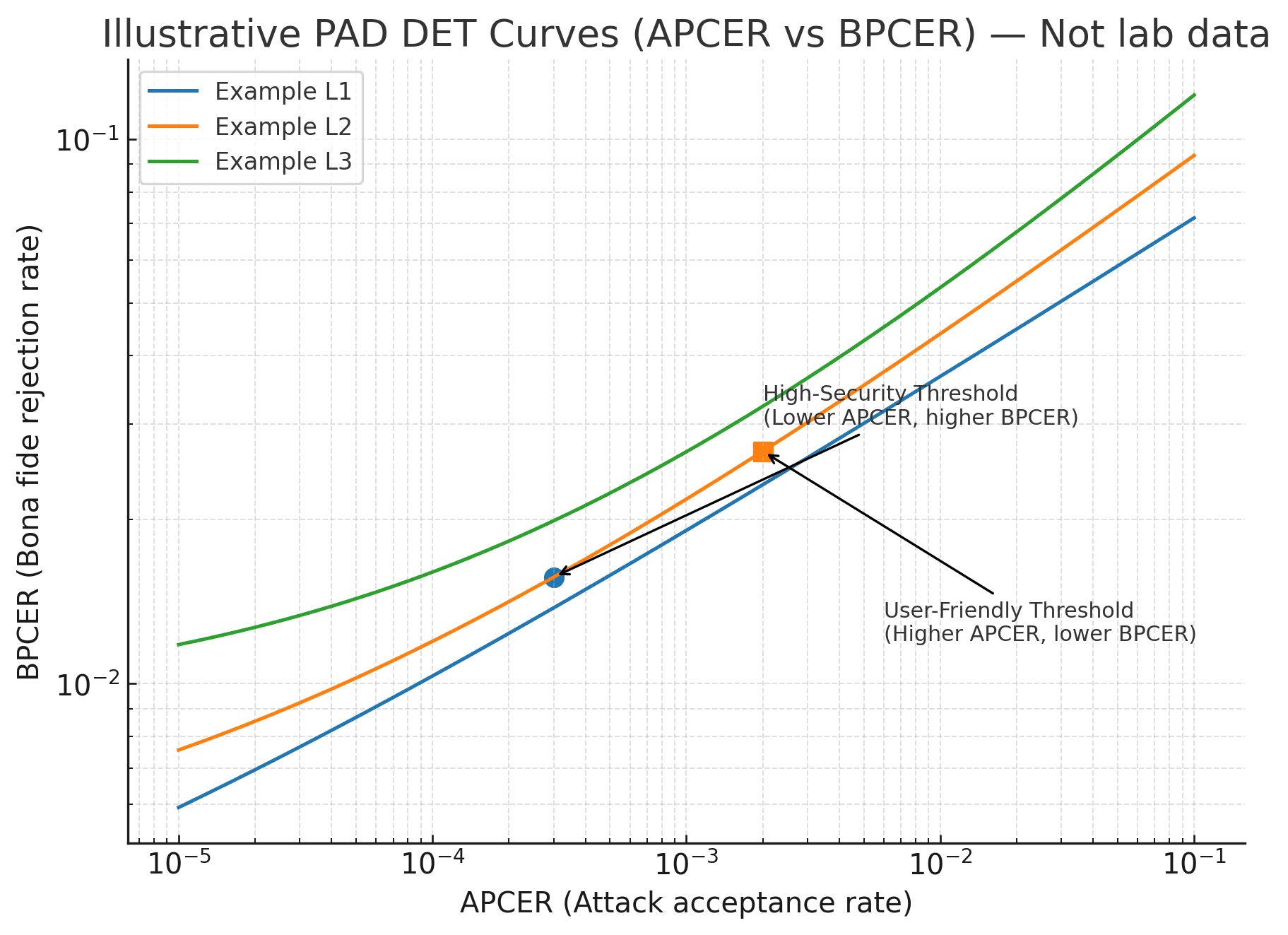
| "APCER alone is enough." | No-buyers need ROC/DET curves showing APCER vs BPCER trade-offs to set thresholds. |
For Buyers: What to Ask Vendors
When evaluating PAD claims, include these in your RFPs or procurement checklist:
What PAD level is certified (L1, L2, or L3)?
When was the certification issued-and is it current?
Did testing cover real-world use cases (mobile, kiosks, border control)?
Are test reports available for review (with ROC/DET curves)?
ROC Curve Visual – illustrates trade-offs between false accepts (APCER) and false rejects (BPCER).
Fast-Start Checklist (Downloadable PDF)
Use this in your RFPs and vendor evaluations:
It covers:
Scope & modality (Face/Fingerprint/Iris; Subsystem vs Full-system; L1/L2/L3).
PAI coverage (species, attempt counts, inclusion of unknown PAIs).
Acquisition conditions (lighting, sensors, cooperative vs uncooperative).
Reporting metrics (APCER, BPCER, IAPAR; ROC/DET curves).
Governance (lab accreditation, ISO versions, product/firmware tested).
Operationalization (thresholds by risk tier, fail-secure behavior, SLA updates).
Conclusion
The informed buyer understands that a lab test, like those conducted by iBeta, is a vital but controlled snapshot of a device's capabilities. True security diligence requires looking beyond the certificate and asking the tough questions: What specific level was passed? How recent is the test? And most importantly, can the vendor provide the full test report, complete with the ROC/DET curves that reveal the real-world trade-offs between security (APCER) and user convenience (BPCER)? Ultimately, matching the certified PAD level to your organization's specific threat model is the only way to ensure your investment delivers genuine security and builds lasting trust in your biometric infrastructure.
Comments