
Understanding Fingerprint Scanner Security and Spoof Detection
The trend in identity management is to replace passwords with biometric solutions. Fingerprint recognition, in particular, is gaining popularity across various platforms, including mobile devices, owing to its simplicity and perceived security. However, people frequently dispute the effectiveness of fingerprint security.
Concerns About Fingerprint Security.
Many are concerned about the security of fingerprint systems: Is it secure enough? What happens if someone replicates my fingerprints? The millions of people who rely on fingerprint verification but are apprehensive about its security understand the feasibility of these scenarios.
Vulnerabilities in fingerprint scanners.
Fingerprint scanners, while more safe and efficient than ever, are acceptable. Here are some of the principal vulnerabilities:
Susceptibility to Presentation Attacks:
Fake fingerprints can be created with simple materials to fool scanners. Although high-end scanners with advanced spoof detection features exist, they are often more costly.
Adaptability Issues:
Fingerprint scanners sometimes struggle with environmental changes. For example, they may have difficulty reading dry fingertips in cold conditions, reducing usefulness.
Environmental Sensitivities:
Scanners are less effective in extreme conditions such as high temperatures or wet environments and require regular maintenance.
Fingerprint spoofing and detection
Fingerprint spoofing involves creating artificial fingerprints to bypass biometric security. This can be accomplished by using high-resolution images of a fingerprint or even latent prints left on surfaces. As scanners have evolved, so too have spoofing methods, with techniques now including 3D printing and materials that mimic the properties of human skin.
Anti-spoofing Techniques
To combat these threats, fingerprint scanners use a variety of anti-spoofing techniques:
Hardware-Based Detection:
These approaches employ physical skin characteristics, such as temperature or electrical conductivity, to determine whether a fingerprint is accurate.
Software-Based Detection:
Techniques include assessing the dynamic changes in the fingerprint pattern or detecting moisture from sweat, which is not present in faked fingerprints.
Static based anti-spoofing analysis.

Image captured by a fingerprint recognition system presented by a fingerprint spoof created with glue. White air bubbles contained in the glue are visible and it exhibits fewer minute details.
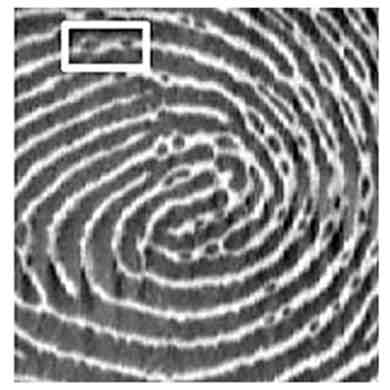
Image captured with a real finger with minute details but no air bubbles.
(Image Credit: Security Research Lab)
Challenges of Ensuring Security
While spoof detection is vital, it is simply one part of a total security plan. Various cybersecurity threats, such as SQL injections, malicious software, and social engineering attacks, compound the risk of spoofing.
Overall Security Strategy
Securing a system involves multiple layers of protection. While a fingerprint scanner may secure a device, the system's cybersecurity vulnerabilities can still pose serious risks.
Multi-Factor Authentication
A Solution Given fingerprint scanners' limitations and the variety of potential security threats, multi-factor authentication emerges as a viable option. Combining something you know (such as a password or PIN) with something you are (such as a biometric scan) can dramatically strengthen system security.
Final Thoughts on Fingerprint Security
Fingerprint biometrics provide a higher level of protection than standard passwords; however, no method is flawless. The best approach for securing identity and information is multi-factor authentication, which combines knowledge-based and biometric features to cover several security bases successfully.
Comments