
Iris recognition is one of the most accurate biometric authentication methods because the iris pattern is complex and cannot be replicated. The National Institute of Standards and Technology (NIST) found that ageing did not influence false non-match errors, even though the dilution effect causes false non-match errors only after decades. For the same reason, iris biometrics is becoming an essential modality in civil ID enrollment, BFSI services, high-security locations, and the health sector. As a contactless biometric authentication technique, it was one of the most convenient modalities to explore during the epidemic.
Iris recognition
An iris is a thin circular diaphragm that lies between the cornea and the lens of the human eye. It has a unique and random pattern that is even visible from a certain distance. The pattern is like a thumbprint, unique for each person and even more accurate than other biometrics since the iris is an internal organ that will never change. An iris recognition scanner reads this unique pattern to authenticate a person. Iris cannot be hindered with contact lenses or eyeglasses. Even blind people can utilize iris recognition technology since it is based on pattern rather than sight.
Steps to enrol an iris
The enrollment procedure may be performed using either single-lens or double-lens iris scanners. A single-lens scanner reads one iris at a time, but a double lens scanner reads both iris at the same time. Because of its simplicity and fast capture of both iris, double lenses are frequently employed for enrolling. Single-lens scanners, on the other hand, are utilized for authentication.
Step 1, Image capture: Enrolling officials capture a high-quality image of the iris using a near-infrared light scanner, resulting in a more precise and detailed image of both iris. Like natural light, incident near-IR does not cause pupil constriction, allowing a complete view of the iris.
Step 2, Quality check: The captured image is shown on the connected computer display. The iris recognition software will go through a quality check then. During this, the software isolates the iris section from the surrounding parts. The check includes the analysis of sharpness, pupil contrast, sclera contrast, dilation, and the presence of any artefacts like eyelashes and eyelid occlusions.
Step 3 Image compression: The cropped image is compressed to the standard template size according to the JPEG 2000 algorithms.
Step 4 template creation: The image in the correct size and quality is used as a template for the database, which will be used for future verification.
Also read: 5 Benefits Of IRIS Recognition Technology
Iris image processing
The process of iris recognition consists of five subprocesses. It includes image acquisition, segmentation, normalization, feature extraction, and code comparison.
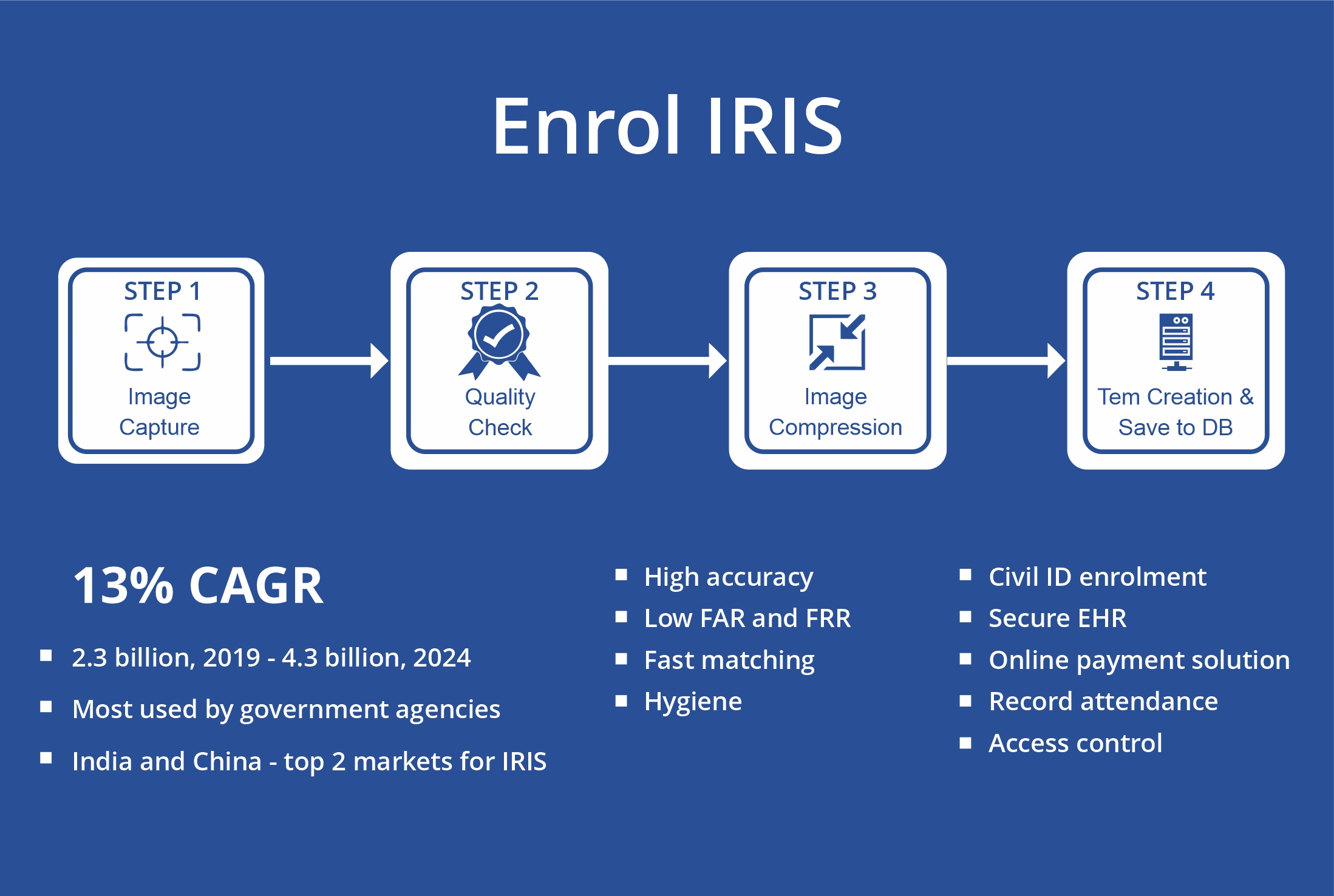
Image acquisition: The iris image is captured using a Near IR camera, a spectral bandwidth in the range of 700-900 nanometers (nm). According to ISO standards, 70% of the iris needs to be visible, and the contrast between the sclera and iris, iris and pupil should be a minimum of 70–50 grey level. The iris diameter of 9.5mm to 13.7mm must have a digital diameter of 100 pixels at the least.
Iris segmentation: Segmenting the iris means isolating the iris region from the background—pupil, eyelids, and eyelashes. The main goal of iris segmentation is to determine the boundaries between the limbic contour that separates the iris from the sclera and the pupillary contour that separates the iris from the pupil. The most commonly used segmentation method is Daugman's Integro-Differential Operator (IDO), which is also known as Iris2pi, which is an algorithm to segment the iris.
Image normalization: Iris image dimension and size may vary due to pupil dilation, scale variance, rotation variance, size of the pupil due to illumination will affect the size of the iris, etc. Normalization is the process employed to avoid the effect of these factors on the image and generate a normalized template. Daugman's rubber sheet method is used for normalization, it transforms the iris image into a flat area. The rubber sheet method finds 32 points that form circles between the inner and outer iris boundaries. Also, 512 points are marked between them to translate the captured data to a dimensionless polar coordinate system. All the points are mapped row-wise to a rectangular matrix.
Iris extraction
The extraction technique is used to extract distinguishing characteristics from the normalized image. The normalized pattern is divided into 128x8 blocks. Each of the 128x8 blocks is filtered with a 2D Gabor filter to extract pattern information, and the phase response of the filter is measured to give iris discriminating information. The template that has a discriminating feature formed is called an "iris code".
In addition, the iris code template is processed for iris masking. Masking is the process of removing the sections of the eyelids that are obscured by reflection, eyelashes, hard contact lenses, and boundary artefacts.
Comparison of iris code
In the final step, the iris code is compared with other templates and identified as a match to authenticate an individual. There are three types of algorithms for iris code comparison: Hamming Distance (HD), Weighted Euclidean Distance (WED), and Normalized Correlation (NC).
Liveness detection: How to know if an iris image is not fake?
Despite the fact that iris recognition is the most reliable and accurate biometric authentication technology, researchers have identified instances of its abuse. People often worry if their iris biometrics may be taken via images or selfies. Some of the iris recognition systems used in smartphones have been hacked in the past. Researchers already had the solution with liveness detection. Liveness detection is the method of determining the actual presence of a subject. There are two approaches to verifying whether the iris is live or not: the software and hardware approach. Both the types read parameters other than the iris pattern to confirm the sample is live.
Software-based liveness detection: Special software algorithms read the image captured by the sensor to detect the liveness. The software identifies a set of discriminant features that allow the construction of an appropriate classifier that provides the probability of an iris being alive or not, based on the extracted set of features.
Hardware-based Liveness detection: It employs extra sensors to determine the liveness of the sample. There are two types of hardware-based detection: voluntary and involuntary behaviour. The device may ask users to blink their eyes or move their iris in any direction during voluntary behaviour examination. On the other hand, the involuntary system will automatically detect the movement of the iris, dilation, or contraction as a response to light, to identify a person.
Closing note:
Iris recognition is a simple and fast authentication process. The subject just needs to look into the iris recognition camera to authenticate. The iris is gaining popularity in healthcare and financial services, and as a contactless authentication method, it is now widely used in attendance management and access control systems. If you are looking for iris devices, either single lens or double lens, please visit us at: IRIS-Sensor or send your inquiry at: Inquiry-Form
Comments