
Introduction
Formal, state-issued identity systems date back to the 19th century. By the late 19th and early 20th centuries many states were experimenting with registration systems, and the world wars accelerated large-scale national registration and identity card use.
Biometrics are now core to many national ID programs (fingerprint, face, iris) because they link a person to a digital credential. One of the most prominent recent national digital-ID moves is China’s National Online (Cyberspace) Identity Authentication Public Service, whose administrative measures came into force on 15 July 2025.
But biometric systems are vulnerable to presentation attacks (photos, video replays, masks, fake fingerprints) and to deep-fakes or synthetic identity attempts. Recent research and reviews show presentation-attack detection (PAD) is an active field.
Why National ID Programs Need Anti-Spoofing?
National ID systems have evolved to biometric-backed digital identities with new threats such as deepfakes, generative AI, along with other high-resolution replication techniques entirely. According to Identity Theft Resource Center’s 2024 Data Breach Report, there were 3,158 data compromise events resulting in more than 1.3 billion victim notices — and fully 84 % of those breaches involved sensitive records. Without anti-spoofing for national ID programs, these attacks succeed at alarming rates.

-
The rise of synthetic identities
Deepfake videos, printed silicone fingerprints, and even 3D-printed facial masks can now deceive standard verification systems. Without anti-spoofing defences, biometric databases become fertile ground for synthetic enrolments.
-
The high stakes of national-scale compromise
When a biometric system is spoofed at national scale, it undermines the integrity of the entire digital identity ecosystem from e-governance to financial inclusion schemes, compromising welfare programs, border control, and national security.
-
The limits of unimodal authentication
Relying on a single biometric trait increases exposure to presentation attacks. A face image can be replayed; a fingerprint can be lifted; an iris can be captured with a high-zoom camera. The need to have independent modalities cross-verify each other is important.
-
Anti-spoofing as a trust enabler
Anti-spoofing technologies from depth sensors and IR imaging to AI-based liveness detection help ensure that each verification is not only correct but also genuine. Citizens are more willing to adopt digital ID systems when they believe their biometrics can’t be easily faked, reused, or stolen.
-
Evolving from detection to prevention
Modern anti-spoofing systems are known to prevent false enrolment at the source. Real-time PAD modules, sensor-level anomaly detection, and multimodal fusion algorithms now block synthetic or replayed inputs before they enter the national database.
-
A new frontier in digital injection
A digital injection attack can manipulate the digital verification stream itself, injecting falsified data directly into the system. AI-generated videos are inserted into the live verification feed, stolen biometric are replayed to authentication servers to impersonate legitimate users.
Also Read - Injection Attacks: The Hidden Threat You Haven't Heard Of
How Anti-Spoofing Technology Works?
At its core, anti-spoofing in national ID systems comes down to one simple principle which is making sure the person standing in front of a biometric scanner is real. Here anti-spoofing filters biometric data streams. Each data point is checked for authenticity before it’s allowed to interact with the main identity database.
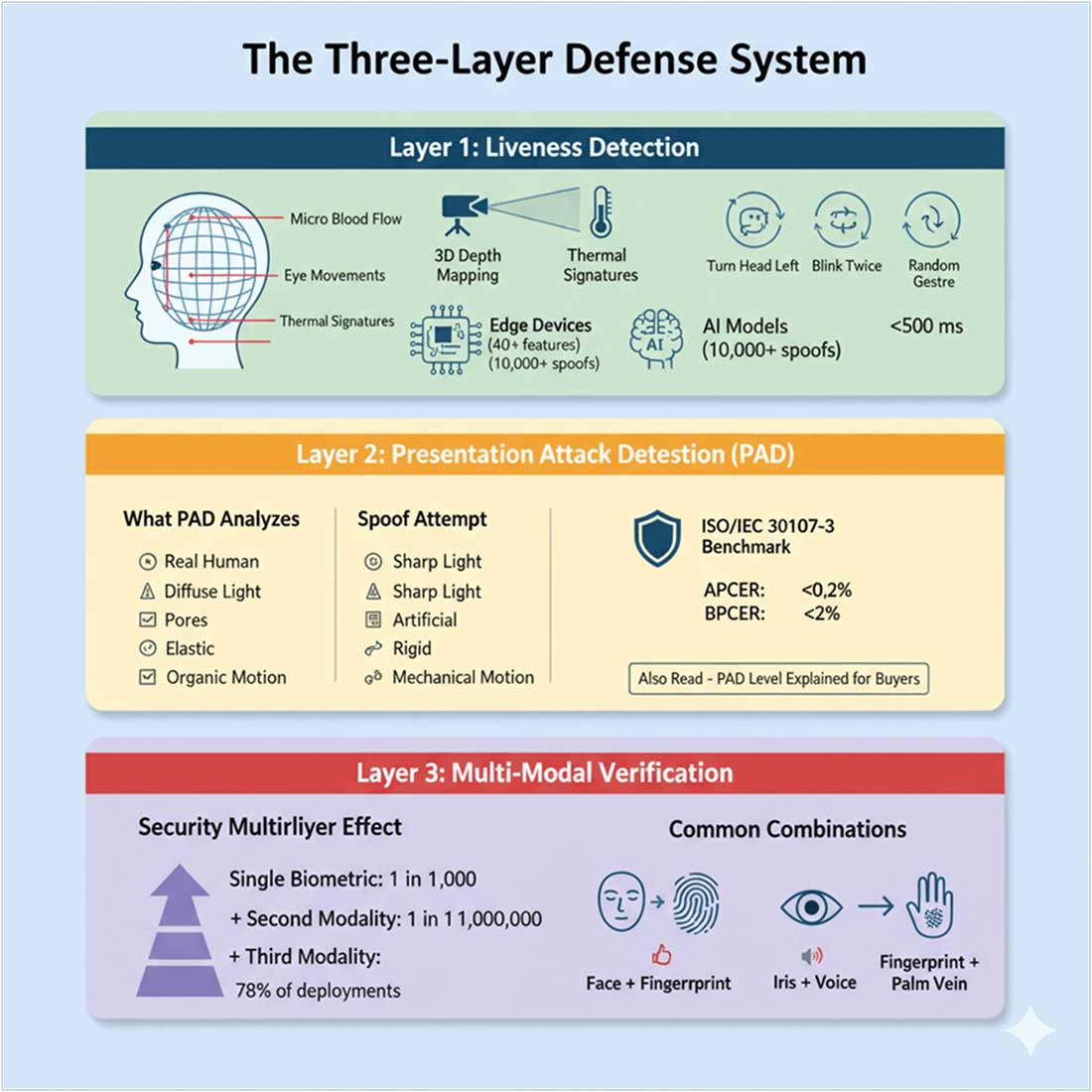
To keep that trust intact, three foundational pillars form the heart of modern anti-spoofing: liveness detection, presentation attack detection (PAD), and multi-biometric modality.
Layer :
Anti-spoofing technology works by making sure the person in front of a biometric scanner is real and not a photo, video, or mask. It does this through a step-by-step defence process that checks every biometric signal before it reaches the main identity database. The first step is called liveness detection. It looks for natural signs of life such as blood flow under the skin, small eye movements, and body heat. Some systems even ask users to blink, turn their head, or perform a quick gesture to confirm they’re physically present. With the help of AI and 3D depth sensors, these systems can tell the difference between a real person and a flat image in just a few milliseconds.
Layer :
The second layer is called Presentation Attack Detection, or PAD. This layer digs deeper to spot any fake or mechanical attempts to fool the system. It studies how light interacts with the skin, how elastic or textured the surface looks, and whether the motion appears natural or artificial. If the scanner detects something stiff, shiny, or machine-like, it flags it as a spoof. PAD systems are tested against global standards like ISO/IEC 30107-3 to make sure they’re both accurate and fair, keeping false positives and missed detections extremely low.
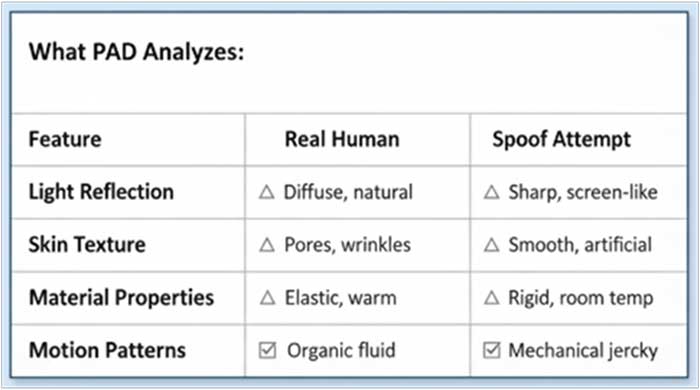
Based on the features of the light reflected from the skin, PAD can analyze whether the data is a spoof or a real human attempt.
Layer :
Finally, the third layer is multi-modal verification, which means using more than one biometric trait to confirm identity. For example, someone’s face can be paired with their fingerprint, or their iris with their voice. Each extra layer makes the system harder to trick—what might be a one-in-a-thousand chance of fooling a single biometric becomes almost impossible when two or three are combined. Together, these three layers form a strong shield that filters fake data, confirms genuine users, and keeps the national identity system safe and trustworthy.
Also Read - PAD Level Explained for Buyers
Implementation Roadmap to National Deployment
This roadmap details a disciplined, four-phase strategy for deploying a secure and inclusive national identity program.
Phase :
Planning
The process begins by mapping every conceivable enrollment and verification touchpoint across the country. This analysis identifies the unique operational challenges and security vulnerabilities of each environment, from a high-traffic urban bank to a remote mobile verification station. This intelligence directly informs the next action: conducting a rigorous financial impact analysis of potential fraud scenarios.
Phase :
Real-World Testing
Two to three competing systems are deployed simultaneously across carefully selected test sites: a dense urban area to test performance under load, a rural community to assess reliability with intermittent connectivity, and a high-security border site to evaluate precision and resilience against sophisticated spoofing attempts. This approach strategically avoids vendor lock-in and stimulates innovation by forcing providers to prove their solutions work under authentic, challenging conditions.
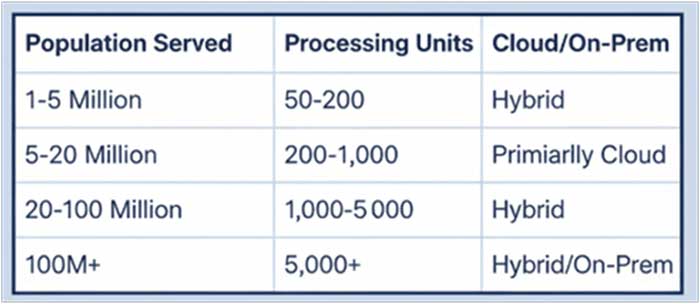
Based on the population or the rollout phase, the National Identity Program can be deployed flexibly.
For the system to be adopted, it must deliver a frictionless user experience, which means a transaction time under 3 seconds and an uptime exceeding 99.5%, ensuring it is always available. Crucially, the technology must be equitable. The mandate for less than 5% accuracy variance across demographic groups is non-negotiable, preventing any form of algorithmic bias.
Phase :
Phased National Rollout
The deployment sequence starts in high-control, high-impact environments like international airports and borders, where lessons can be learned and processes refined quickly. From there, it expands to major urban centers and capital city government offices, leveraging existing infrastructure. Finally, it extends to regional capitals, secondary cities, and ultimately, to the most remote communities, ensuring universal coverage.
Phase :
Data-Driven Improvement
The core of this phase is a comprehensive, real-time monitoring dashboard, which acts as the central nervous system for the entire identity program. This constant stream of data allows operators to predictively identify potential issues. This final commitment to data-driven vigilance ensures the national identity program remains secure, reliable, and trustworthy for generations to come.
Choosing the Best Anti-Spoofing Solution
Here’s how to choose the best anti-spoofing solution by looking for four key certifications. Each one proves the technology is excellent in a different, crucial way.
-
Check for Rock-Solid Security Against Attacks
First and foremost, the solution must be tough to break. Look for the iBeta Level 2 PAD certification. This is the industry's "gold standard" and proves the system has been rigorously tested against more than 1,000 different types of physical attacks. In simple terms, it means the system is highly effective at stopping someone who tries to fool it with a fake photo, a video, or a mask.
-
Ensure It Meets Global Standards
Next, a great solution must be recognized and legally sound on an international level. That’s what the ISO/IEC 30107-3 certification guarantees. This tells you the technology meets global standards for Presentation Attack Detection (PAD). It’s your proof that the system is built to work seamlessly with other technologies worldwide and will stand up to legal scrutiny.
-
Demand Fairness and Accuracy
A system is only effective if it works accurately and fairly for everyone. For this, check for NIST FRVT testing. This is the official benchmark used by the U.S. government to test facial recognition technology for both accuracy and demographic bias. This certification is critical because it confirms the technology performs reliably for people of all ages, genders, and ethnicities.
-
Prioritize Privacy and Data Protection

Look for these certifications to be confident you're choosing a solution that is truly secure, reliable, and trustworthy.
Finally, the solution must respect user privacy and comply with the law. A certification for GDPR/Data Residency is essential. This shows the system is designed to operate legally in the European Union and other regions with strict data protection laws. It’s your assurance that the technology handles user data responsibly and ethically.
In short, the best solution will have a proven track record in all four of these areas: tough security (iBeta), global compliance (ISO), fairness (NIST), and privacy (GDPR).
Also Read - Ethiopia National Digital ID Biometric Empowerment
Conclusion
Governments can’t ignore anti-spoofing in national ID programs anymore. Identity fraud is evolving fast, powered by AI-generated fingerprints and realistic deepfakes that threaten even secure systems. Without strong liveness detection, the most advanced biometric setups can still be fooled. Anti-spoofing ensures that every authentication truly connects to a real person not an imitation or digital copy. For nations investing in digital governance, the goal for implementing National Identity Programs has moved beyond building identity databases. Anti-spoofing makes that trust possible.
FAQs
Anti-spoofing is a security feature that stops fake or copied biometrics from being used in national ID systems. It makes sure that only real, live human traits—like a genuine fingerprint, iris, or face—are accepted. It detects fake attempts such as silicone fingerprints, printed photos, or 3D masks. This protects digital ID systems like Aadhaar from identity theft and keeps citizen data safe.
Regular biometric verification only checks if a fingerprint, face, or iris matches the saved record. Anti-spoofing goes further. It checks if the biometric comes from a real person by looking for signs of life, like skin texture, temperature, or blinking. Regular verification confirms identity; anti-spoofing confirms liveness. Together, they stop fake attempts and make national ID systems more secure.
Yes. Modern anti-spoofing works even without internet. Devices with on-device liveness detection can verify users locally. When the connection returns, results are synced with the main server. This helps rural and remote areas use secure ID verification without needing constant connectivity.
Security and speed can work together with good hardware and software design. Devices that have built-in anti-spoofing and encryption process data faster because they work locally. Using simple methods like caching and pre-checks also saves time. This way, verification stays fast for places like airports and banks while keeping data safe.
Vendor lock-in happens when a government or company depends on one supplier’s system and cannot switch easily. This happens when data is stored in closed formats, APIs are not shared, or hardware only works with one vendor’s software. Without exit clauses, costs rise over time. To avoid lock-in, use open standards, transparent APIs, and hardware that works with many systems. Always include clear exit terms in every contract.